How Threat Hunting Can Get Your Security Investments Moving in the Right Direction
The scouts have a saying: "Know before you go." While it's always prudent to plan your route, our ...
Read More
The scouts have a saying: "Know before you go." While it's always prudent to plan your route, our ...
Read More
According to the General Data Protection Regulation (GDPR), an entity must have a "valid lawful ...
Read More
Let me tell you a story about a recent DFIR investigation I was fortunate enough to be involved ...
Read More
The General Data Protection Regulation (GDPR) affects all organizations that do business with the ...
Read More
Of all the time sucks that security professionals face, arguably one of the more underrepresented ...
Read More
Scour the World Wide Web for articles on what keeps CISOs up at night, and you'll return a list so ...
Read More
The recently released 2018 Security Pressures Report from Trustwave highlighted the diverse points ...
Read More
Johan Hagdahl, director of Trustwave global compliance and risk services, offers guidance to ...
Read More
Recently I took my car in for a service - that, in itself, isn't earth shattering. But it led me to ...
Read More
As major milestone dates imposed by the pioneering and prescriptive New York State Department of ...
Read More
A respected CIO in Australia recently came to us. He had been in the role for more than two years, ...
Read More
In a year that delivered a steady stream of breakdowns, tumult and facepalms to the world of ...
Read More
Considering how easily prevention-centered security can be defeated, your organization is hopefully ...
Read More
About five years ago, a spiritual friend encouraged me to start each day by reaching for a bedside ...
Read More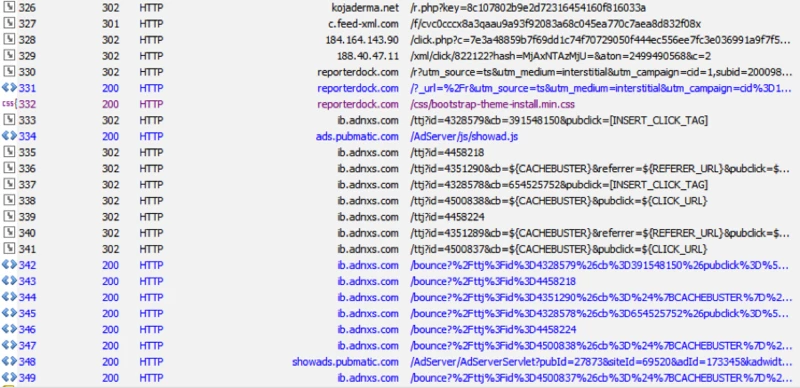
When you think about cyberattacks and your business falling victim to one, chances are your mind ...
Read More
New laws across the world are placing the spotlight on data security and privacy. Here in the ...
Read More
Even when all hell breaks loose in the world of information security, it has never rivaled the ...
Read More
Three years ago, I devoted a blog post to the alarming uptick in exploit kit attacks, specifically ...
Read More
Cybercriminals are hastening their use of methods and malware that are intended to evade detection. ...
Read More
If you're on the right side of the law, yet you still believe that the solution to hackers is more ...
Read More
There is an adage in sports that defense win championships. The premise behind the axiom goes ...
Read More
Our just-released Trustwave Global Security Report reveals significant developments for the ...
Read More
The global WannaCry ransomware outbreak helped steer much-needed mainstream conversation toward the ...
Read More
Recently I heard from a CISO who described the state and mood of his IT security team when he ...
Read More
Like other professions that are not fully understood by the rest of the organization, cybersecurity ...
Read More
When you think of hot industry targets for cybercriminals, there are obvious ones that come to mind ...
Read More
You've seen it in the movies: Seemingly legitimate businesses such as restaurants, dry cleaners and ...
Read More
When it comes to measuring the pressures you are under as an IT security professional, arguably the ...
Read More