SpiderLabs – The Year in Review
It’s not exactly a secret that 2020 hasn’t been a year to remember fondly – to put it mildly. But ...
Read More
It’s not exactly a secret that 2020 hasn’t been a year to remember fondly – to put it mildly. But ...
Read More
As Trustwave celebrates its 25th anniversary, we’ve spent some time looking back at the history of ...
Read More
To celebrate the 25th anniversary of Trustwave, we wanted to look back at how our profession has ...
Read More
November 2020 marks a special month for Trustwave as we celebrate our 25th anniversary. It’s been a ...
Read More
As the Trustwave Marketing Director for the Asia Pacific (APAC) region, I wanted to learn more ...
Read More
For all kinds of organizations, the shift toward the cloud is accelerating. In fact, Gartner ...
Read More
In cybersecurity, it can be said that the only constant is change. Every year, the pace of ...
Read More
As organizations around the world and across all industries wage the never-ending fight against ...
Read More
As the COVID-19 pandemic continues to force organizations all over the world to adopt varying ...
Read More
Security Orchestration, Automation and Response (SOAR) is an oft-discussed term in discussions ...
Read More
Keeping data secure is one of the key cybersecurity challenges that organizations of all types, and ...
Read More
I loved reading the blog post Threat Hunting: Taking the First Step to Restoring Cyber Hygiene ...
Read More
Cybersecurity teams are overloaded on multiple fronts with an ever-increasing pressure to keep up ...
Read More
When the Department of Defense (DOD) and its governmental partners announced the Cybersecurity ...
Read More
The COVID-19 pandemic has wreaked havoc on the world, causing previously unimaginable human ...
Read More
The last week has been a wake-up call to the country and the world. Recent tragic events like the ...
Read More
A chief financial officer (CFO) is a necessary component required to ensure a cybersecurity ...
Read More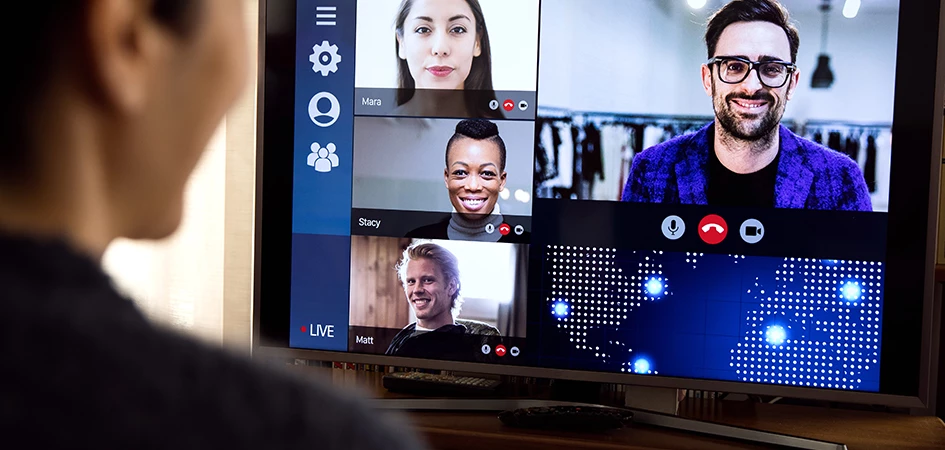
There has been a plethora of articles in the media recently about security issues in the Zoom ...
Read More
The legal department is an increasingly important presence when it comes to making cybersecurity ...
Read More
Don’t have a team of security experts and trained incident responders ready to respond and ...
Read More
The Department of Defense (DoD) has officially published version 1.0 of its Cybersecurity Maturity ...
Read More
As we kick off the New Year, Defense Industrial Base (DIB) and its 300,000+ members are legally ...
Read More
[Author note: 2019-20 has had one of the most horrific fire seasons on record in Australia, with ...
Read More
It’s been another lap around the sun for the cybersecurity industry, filled with great ...
Read More
Security professionals, legislators, and relevant industries have been calling for greater ...
Read More
The days when security departments set up alarms just to sit and wait for alerts are long gone. ...
Read More
As the threat landscape evolves, so does the security industry. The problem is that it’s changing ...
Read More
Organizations are evolving at an alarming rate. With the evolution of handheld technology flooding ...
Read More