Now is the time to Partner With Trustwave MDR
Trustwave Managed Detection and Response (MDR) is one of the most important cybersecurity offerings ...
Read More
Trustwave Managed Detection and Response (MDR) is one of the most important cybersecurity offerings ...
Read More
Trustwave has created new Managed Detection and Response (MDR) services to deliver unmatched ...
Read More
2022 has been busy in the cyber world. While there were signals in 2021 with the increased in ...
Read More
SC Media and SC Media Europe have named Trustwave as a finalist for several awards to be announced ...
Read More
Most organizations employ mobile computing, which utilizes wireless communications for staff ...
Read More
The Russian invasion of Ukraine has heightened government and business awareness around the reality ...
Read More
Email security is not a simple check-box item. The need to have a strong email security solution in ...
Read More
The threats facing databases today are numerous and constantly evolving as the perimeter continues ...
Read More
As we approach the one-year anniversary of the Colonial Pipeline ransomware attack, it is an ...
Read More
There is a bit of serendipity associated with World Password Day 2022. This year the day falls on ...
Read More
Let's dive head-first into this new security acronym, XDR, or extended detection and response. ...
Read More
There are a variety of methods that an organization can implement to test its ability to withstand ...
Read More
Gartner has recognized Trustwave as a Representative Vendor in the analyst firm’s March 2022 Market ...
Read More
By Gary Abad, Vice President of Global Channels and Alliances, Trustwave
Read More
The overnight move to remote and hybrid work models instantly created a more complex infrastructure ...
Read More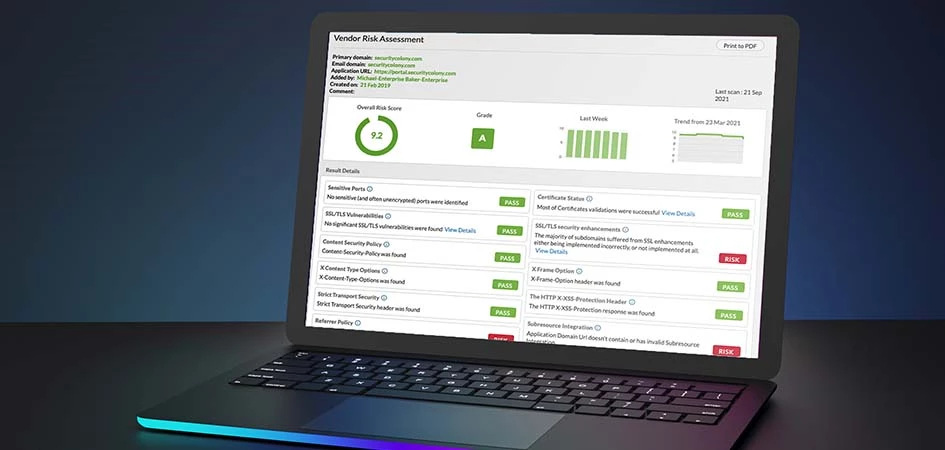
This is the second installment in Trustwave’s in-depth tour of our Security Colony platform. For a ...
Read More
Maintaining cyber resilience across your ecosystem is a significant challenge that must not be ...
Read More
The dangers of email security are often understated. One successful email attack can lead to ...
Read More
The ongoing war between Russia and Ukraine has placed organizations worldwide on full alert due to ...
Read More
This is the second in a series of blogs that describes the importance and inner workings of ...
Read More
Home improvement stores like Home Depot and Lowes are the lifeline for a lot of contractors looking ...
Read More
Every woman in cybersecurity should be empowered. Cybersecurity innovation thrives on diversity of ...
Read More
A critical part of improving a business’ cyber resilience is ensuring staff, including the ...
Read More
In this episode of the Trustwave CISO Bytes Podcast, host David Bishop, Chief Information Security ...
Read More
I have seen quite a few articles of late proclaiming that a major cyberattack against Australia is ...
Read More
There is more to implementing a successful cybersecurity training program than to task IT with the ...
Read More
It's somehow fitting that Groundhog Day and tax scam season overlap.
Read More
Ransomware continued to be the most significant cybersecurity threat facing critical ...
Read More