Resurgence of BlackCat Ransomware
Updated March 8: Based on our experience, we believe that BlackCat's claim of shutting down due to law enforcement pressure is a hoax. We anticipate their return under a new guise or brand after their hiatus. This scam tactic serves as a means for them to execute one final significant scam before resurfacing with less scrutiny.
In today's rapidly evolving cyber landscape, modern adversaries constantly advance their methods to circumvent traditional defenses. At Trustwave, recent observations have unveiled the resurgence of the BlackCat group following its disruption by the US Justice Department on December 19, 2023.
BlackCat’s comeback includes a major attack on February 21 striking Change Healthcare, which is part of Optum and owned by UnitedHealth Group. The group claimed to have stolen 6TB of data from Change Healthcare, according to published reports. The attack has caused delays in processing payment claims, forcing customers to pay out of pocket for services and in some cases not allowing prescriptions to be filled.
The group has adeptly leveraged legitimate remote access tools, in conjunction with unique tokens, to execute a sophisticated ransomware variant. This strategy underscores the critical importance of maintaining vigilance and the necessity for organizations to persistently evolve their security measures to effectively combat these ever-changing threats. While exploiting legitimate tools for ransomware deployment is not a novel tactic for BlackCat, our primary focus lies in analyzing detection capabilities and neutralizing these threats.
The initial foothold established by the threat adversary involves the strategic utilization of legitimate remote session management software, such as Total Software Deployment and ScreenConnect. This method enables the adversary to blend in with normal administrative activities, thereby significantly complicating detection efforts. By leveraging these widely used remote management tools, the attacker gains unauthorized access to targeted systems under the guise of legitimate user behavior. Figure 1 shows the initial access activities.
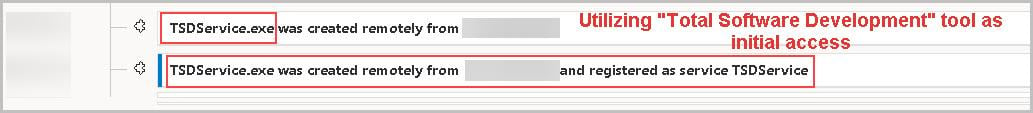
Figure 1: Initial Access via Total Software Development
Upon gaining access, the adversary proceeds to disable security software. This action is meticulously executed, based on a detailed profiling of the target's environment, to ensure that the disabling of security measures does not trigger alerts that could lead to early detection.
The goal of this sophisticated initial access strategy is to deploy a variant of BlackCat ransomware. The deployment is facilitated using access tokens uniquely associated with this ransomware variant, ensuring a targeted and stealthy infection process. These tokens likely provide the ransomware with the necessary permissions to execute and propagate within the compromised network, leveraging the initial foothold to cause maximum disruption.
Functions of BlackCat Ransomware Binary
Our investigation observed that after disabling security products, the threat actor (TA) transferred and executed the BlackCat ransomware binary update.exe. Unlike typical execution processes, this binary requires a 64-character hexadecimal access token for execution; without this token, the binary will not execute. This mechanism is a key component that allows BlackCat to remain stealthy for researchers who may obtain the binaries from other sources without the access token details. It is worth noting that while earlier versions of BlackCat binaries could be bypassed by inputting random tokens, this is not possible with Version 3.
Furthermore, the BlackCat binary provides self-explanatory and straightforward help commands. These commands indicate a focus on reducing noise in the environment and customizing the attack based on the victims. Figure 2 shows the commands displayed from the binary.

Figure 2: Commands listed in the binary
|
Command |
Action |
|
-access-token <ACCESS_TOKEN> |
Access token to execute the payload |
|
--drag-and-drop |
Invoked with drag and drop |
|
--drop-drag-and-drop-target |
Drop drag and drop target batch file |
|
--extra-verbose |
More detailed log |
|
--help |
Help command |
|
--log-file <LOG_FILE> |
Output the execution events to a file |
|
--no-impers |
Do not spawn impersonated processes on Windows |
|
--no-net |
Do not discover network shares on Windows |
|
--no-prop |
Do not self propagate (worm) on Windows |
|
--no-prop-servers <NO_PROP_SERVERS> |
Do not propagate to defined servers |
|
--no-vm-kill |
Do not stop VMs on ESXi |
|
--no-vm-kill-names <NO_VM_KILL_NAMES> |
Do not stop defined VMs on ESXi |
|
--no-vm-snapshot-kill |
Do not wipe VMs snapshots on ESXi |
|
--no-wall |
Do not update desktop wallpaper on Windows |
|
-p,--paths <PATHS> |
Only process files inside defined paths |
|
--prop-file <PROP_FILE> |
Propagate specified file |
|
--safeboot |
Reboot in Safe Mode before running on Windows |
|
--safeboot-instance |
Run as safeboot instance on Windows |
|
--safeboot-network |
Reboot in Safe Mode with Networking before running on Windows |
|
--sleep-restart <SLEEP_RESTART> |
Sleep for duration in seconds after successful run and then restart. |
|
--sleep-restart-duration <SLEEP_RESTART_DURATION> |
Keep soft persistence alive for duration in seconds. (24 hours by default) |
|
--sleep-restart-until <SLEEP_RESTART_UNTIL> |
Keep soft persistence alive until defined UTC time in millis. |
|
--ui |
Show user interface |
|
-v,--verbose |
Log to console |
Table 1: Full command lists of Blackcat binary
Analysis of BlackCat Ransomware Binary Execution and Commands
After gaining a foothold in the system, the threat actor executed a batch script to disable Windows Defender. The script contained a series of commands specifically designed to undermine the security measures. By doing so, the actor also disabled SmartScreen, further weakening the system's defenses. This action left the machine vulnerable to further exploitation and manipulation. The disabling of these security features is a common tactic threat actors employ to avoid detection and maintain persistence. Figure 3 shows the outcome of the batch script execution.
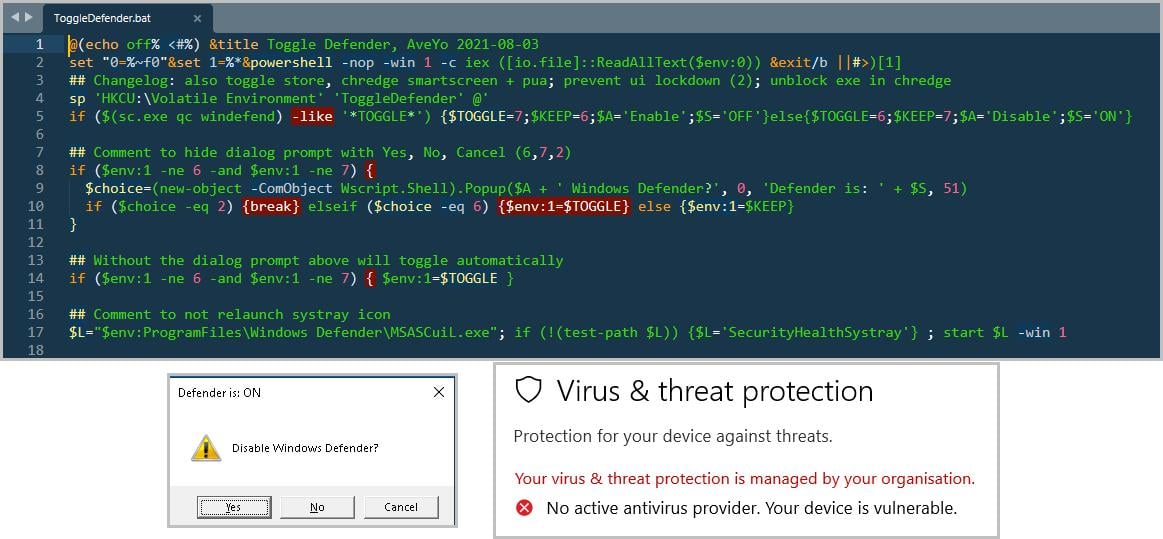
Figure 3: Outcome of the batch script execution
update.exe -v --no-net --no-prop --access-token <64 character hexadecimal>
- -v - Verbose, log the output in the console
- --no-net - Do not discover network shares on Windows
- --no-prop - Do not self-propagate (worm) on Windows
- --access-token - Valid access token to execute the ransomware binary
The threat actor intentionally reduces the ransomware's noise to avoid detection. Their goal is to prevent the malware from spreading across shared drives. This approach helps to prevent the ransomware from behaving like a worm-type malware.
The BlackCat ransomware binary, compiled in Rust, presents complexities in analysis. We have reverse-engineered the file to comprehend its functions. Notably, the binary possesses logging capabilities, facilitating the initial triage by providing insights into the binary's activities during execution. Figure 4 shows the logging capabilities.
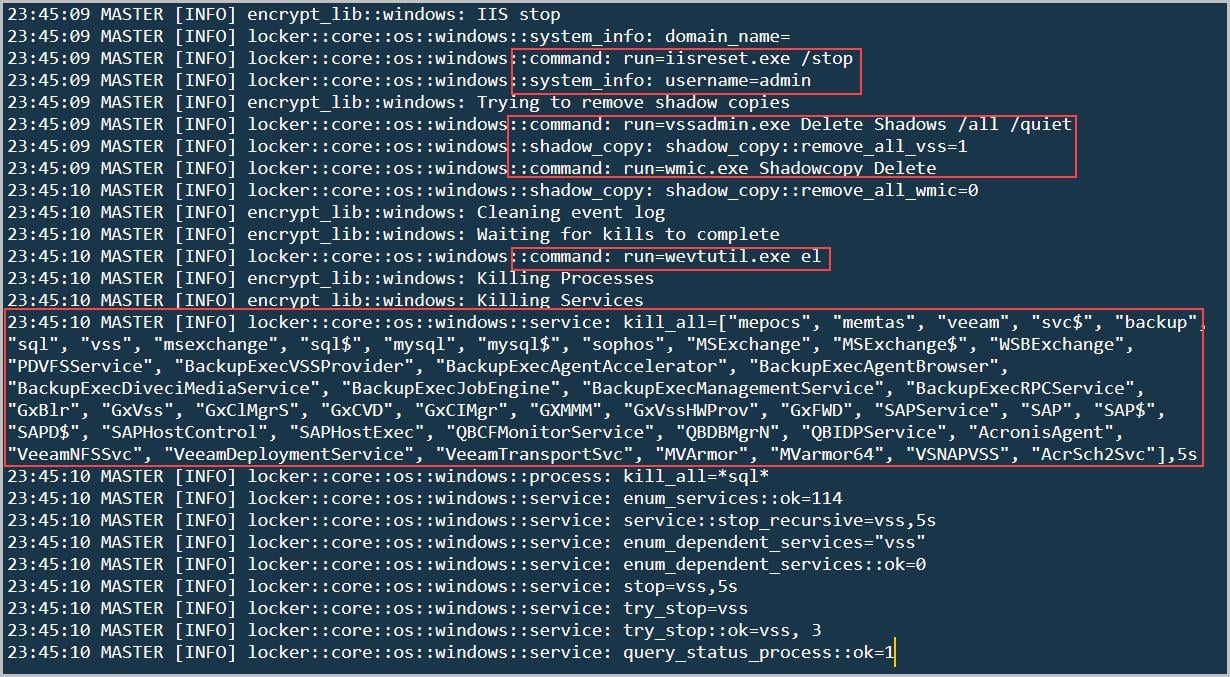
Figure 4: Logging capabilities
The ransomware binary attempts to perform privilege escalation when it is not executed with elevated permissions.
Elevation: Administrator!new:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}
Obtains administrative-level privileges by instantiating a new COM (Component Object Model) object using its CLSID (Class Identifier).
Token Impersonation - The ransomware binary queries the user's privileges using the LookupPrivilegeValueW function. Some of these privileges include:
"SeIncreaseQuotaPrivilege" "SeTakeOwnershipPrivilege" "SeTakeOwnershipPrivilege" "SeSystemProfilePrivilege" "SeSystemtimePrivilege" "SeProfileSingleProcessPrivilege" "SeProfileSingleProcessPrivilege" "SeIncreaseBasePriorityPrivilege" "SeRestorePrivilege" "SeBackupPrivilege"
Privileges such as SeRestorePrivilege and SeBackupPrivilege can be exploited for credential dumping through backups of the SYSTEM and SAM files. The extracted credentials are then utilized for lateral movement, such as leveraging the NT hash of the domain's KRBTGT account. Figure 5 shows the privilege escalation activities, Figure 6 shows the debugging of LookupPrivilegeValueW function.
 Figure 5: Privilege Escalation
Figure 5: Privilege Escalation
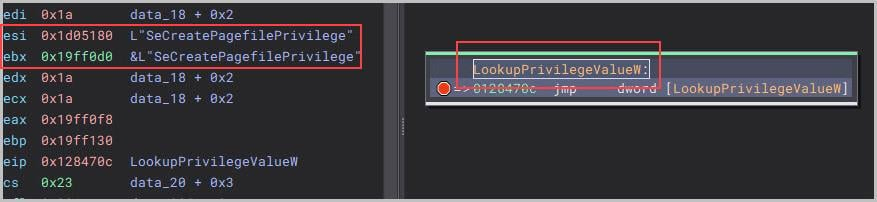
Figure 6: Debugging LookupPrivilegeValueW function
The ransomware binary initiates a search for any concealed partitions and mounts them. This procedure is executed to encrypt all files on the disk, encompassing those located within hidden partitions.
We found that the binary establishes a NamedPipe connection named \__rust_anonymous_pipe1__.[PID_of_Process].[RandomNumber] through the CreateNamedPipeW function. For instance, one of the NamedPipe connections observed is \__rust_anonymous_pipe1__.1566.4308904526.
Upon creation of the NamedPipe, it executes a command and directs the output to the newly created NamedPipe. This process is repeated for each command, with a new NamedPipe being created for the output of each command.
"cmd" /c "wmic csproduct get UUID" - Retrieve the unique identifier of the host, Figure 7 shows how the NamedPipe connections are used.
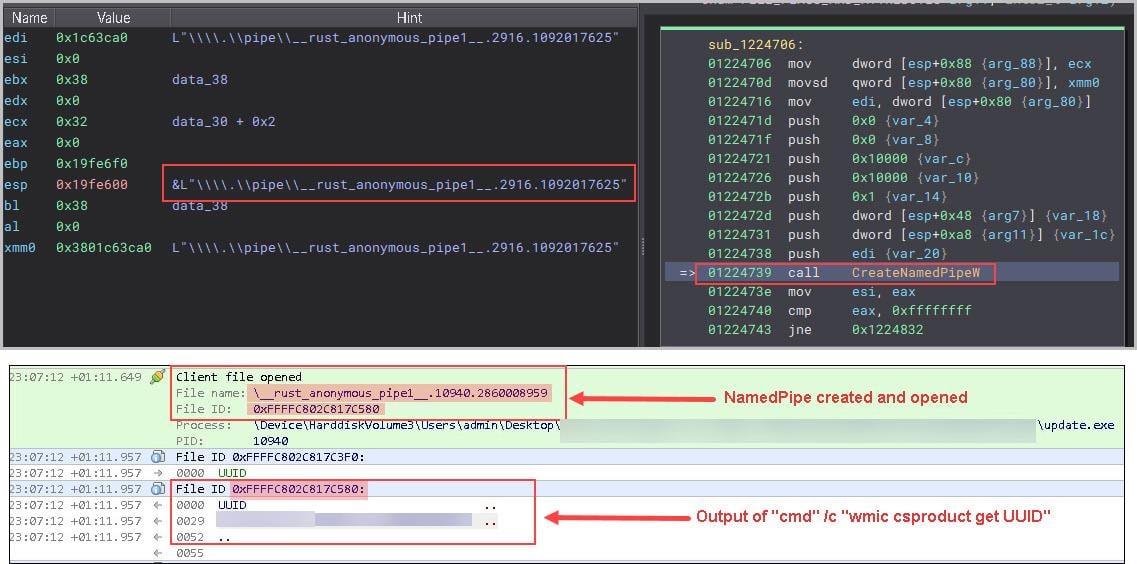
Figure 7: NamedPipe connections
Arp -a – To list active known IP addresses. Figure 8 shows the output of arp -a command output, it will then route back to the created NamedPipe.
 Figure 8: Output of arp -a command
Figure 8: Output of arp -a command
"cmd" /c "iisreset.exe /stop" - Stopping IIS services on the host is a critical step if ransomware has been deployed on the server, as this can lead to significant service disruption.
powershell.exe -encodedCommand ZgBvAHIAZQBhAGMAaAAgACgAJABpACAAaQBuACAAJAAoAGMAbQBkAC4AZQB4AGUAIAAvAGMAIABzAGMAIABxAHUAZQByAHkAZQB4A[Redacted for Brevity] ByAGUAcwBlAHQAIAAvAHMAdABvAHAA
foreach ($i in $(cmd.exe /c sc queryex type= service state= all | findstr SERVICE_NAME | ForEach-Object {$.Split(":")} | ForEach-Object {$.Split(" ")}| findstr -i sql)){echo Y | net stop $i};iisreset /stop
The decoded script shows that, the PowerShell script is designed to terminate all services associated with SQL Server and IIS.
"cmd" /c "reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters /v MaxMpxCt /d 65535 /t REG_DWORD /f"
The MaxMpxCt setting sets a limit on how many tasks the server can work on at the same time. Setting it to 65535 brings it to the highest limit possible, helping the server handle lots of tasks all at once.
"cmd" /c "vssadmin.exe Delete Shadows /all /quiet" - Delete all volume shadow copies (Backups) without displaying any output. Figure 9 shows the command execution of deleting volume shadow copies.
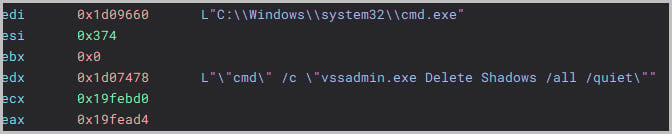
Figure 9: deletion of volume shadow copies
"cmd" /c "wmic.exe Shadowcopy Delete" - Delete all volume shadow copies (Backups) using WMIC.
Killing the virtualization services to disrupt the service - "mepocs", "memtas", "veeam", "svc$", "backup", "sql", "vss", "msexchange", "sql$", "mysql", "mysql$", "sophos", "MSExchange", "MSExchange$", "WSBExchange", "PDVFSService", "BackupExecVSSProvider", "BackupExecAgentAccelerator", "BackupExecAgentBrowser", "BackupExecDiveciMediaService", "BackupExecJobEngine", "BackupExecManagementService", "BackupExecRPCService", "GxBlr", "GxVss", "GxClMgrS", "GxCVD", "GxCIMgr", "GXMMM", "GxVssHWProv", "GxFWD", "SAPService", "SAP", "SAP$", "SAPD$", "SAPHostControl", "SAPHostExec", "QBCFMonitorService", "QBDBMgrN", "QBIDPService", "AcronisAgent", "VeeamNFSSvc", "VeeamDeploymentService", "VeeamTransportSvc", "MVArmor", "MVarmor64", "VSNAPVSS", "AcrSch2Svc”
wevtutil.exe el - Clearing Windows event logs by reading the output from an opened NamedPipe containing a list of event logs to check and delete, that is depicted in Figure 10.

Figure 10: List of event logs to check and delete
Files are being encrypted with an extension (masked for security reasons), and a ransom note named 'RECOVER-[masked]-FILES.txt.png' is being dropped, along with a change in the desktop wallpaper. Our research has uncovered a decrypter for a different extension capable of decrypting files using a private key. The only method to decrypt the files is by utilizing the private key corresponding to the specific public key assigned to the ransomware binary. Figures 11 and 12 show the ransom note dropped in the folder’s wallpaper changed with ransom note. The extension and the ransomware portal link are redacted for security purposes. Figure 13 shows the decrypter in action but on older versions.
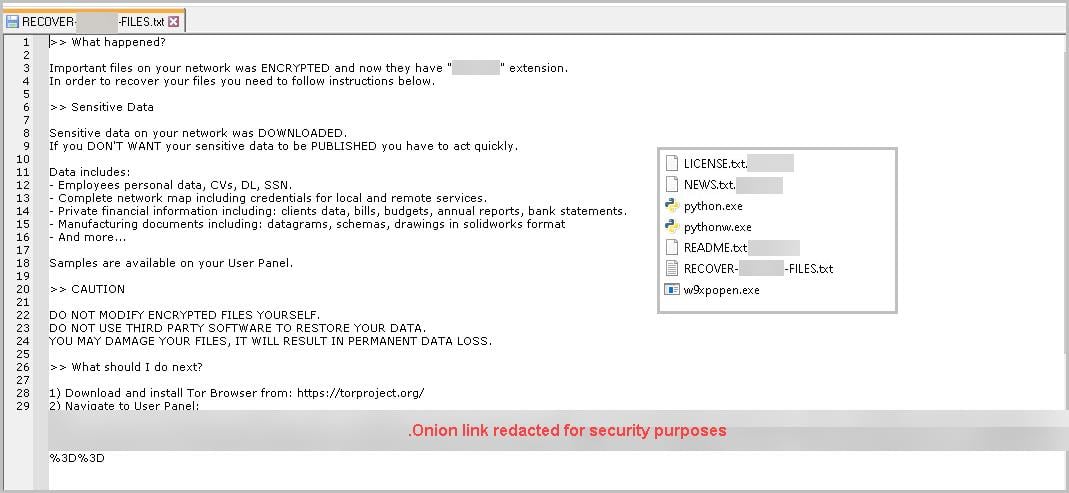
Figure 11: Ransom note
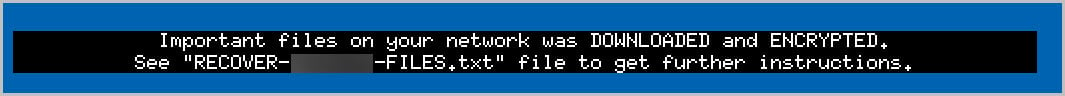
Figure 12: Desktop wallpaper with ransom note
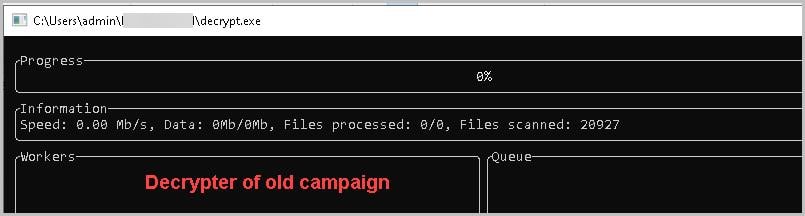
Figure 13: decrypter of old campaign

Figure 14: Ransomware portal for the payment
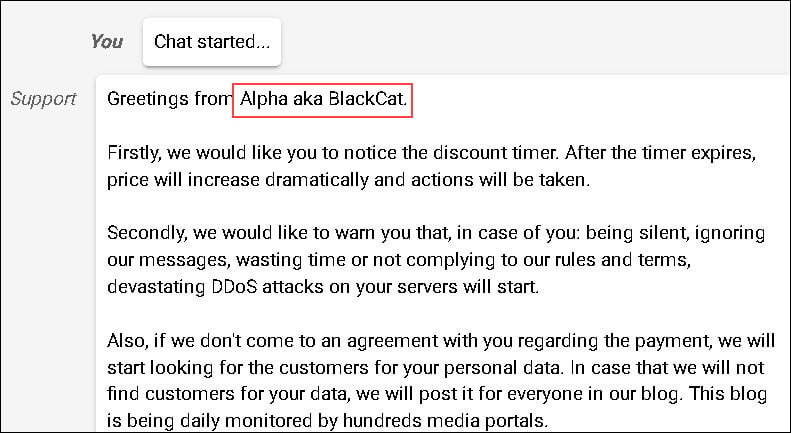
Figure 15: BlackCat chat page
Currently, no transactions have been observed in cryptocurrency coins. It is unclear whether this is specific to the target or to the current campaign. To evade heuristic behavior detection and prevent damage to the victim's machine, BlackCat ransomware deploys a folder exclusion list to avoid encrypting files within those specified directories.
MITRE Detections:
|
Tactics |
Techniques |
ID |
|
Execution |
Command and Scripting Interpreter |
|
|
Shared Modules |
||
|
System Services: Service Execution |
||
|
Persistence |
Create or Modify System Process: Windows Service |
|
|
System Shutdown/Reboot |
||
|
Privilege Escalation |
Access Token Manipulation |
|
|
Access Token Manipulation: Token Impersonation/Theft |
||
|
Defense Evasion |
Abuse Elevation Control Mechanism: Bypass User Account Control |
|
|
File and Directory Permissions Modification |
||
|
Indicator Removal: Clear Windows Event Logs |
||
|
Indicator Removal: File Deletion |
||
|
Obfuscated Files or Information |
||
|
Obfuscated Files or Information: Indicator Removal from Tools |
||
|
Process Injection |
||
|
Virtualization/Sandbox Evasion: System Checks |
||
|
Discovery |
Account Discovery |
|
|
File and Directory Discovery |
||
| Network Share Discovery | ||
|
Process Discovery |
||
|
Query Registry |
||
|
Software Discovery |
||
|
System Information Discovery |
||
|
System Network Configuration Discovery |
||
|
System Network Configuration Discovery: Internet Connection Discovery |
||
|
System Owner/User Discovery |
||
|
Command and Control |
Remote Access Software |
|
|
Proxy: Multi-hop Proxy |
||
|
Exfiltration: |
Transfer Data to Cloud Account |
|
|
Impact |
Inhibit System Recovery |
|
|
Service Stop |
||
|
System Shutdown/Reboot |
Table 2: MITRE Detections
Conclusion
This method of gaining initial access and deploying ransomware highlights the evolving tactics of cyber adversaries, who increasingly leverage legitimate tools and detailed profiling to bypass traditional security defenses. It underscores the need for continuous monitoring, behavior analysis, and the adoption of a zero-trust security model to detect and respond to such advanced threats effectively.
Trustwave's recent revamp of its Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts and monitor our customers as this campaign continues. Trustwave offers ACTH as an option in Trustwave's Managed Detection and Response Services. For more information, please read Trustwave Revamps Continual Threat Hunting Enabling Significantly More Hunts and Unique Threat Findings.
ABOUT TRUSTWAVE
Trustwave is a globally recognized cybersecurity leader that reduces cyber risk and fortifies organizations against disruptive and damaging cyber threats. Our comprehensive offensive and defensive cybersecurity portfolio detects what others cannot, responds with greater speed and effectiveness, optimizes client investment, and improves security resilience. Learn more about us.
