Trustwave SpiderLabs “noted” in Part 1 and Part 2 of our OneNote research that OneNote has been used as a malware delivery mechanism now we will shift gears and focus on several OneNote decoy notes SpiderLabs has discovered that deliver malware families like Qakbot, XWorm, Icedid, and AsyncRAT. While the malware payload can change, the techniques have generally been the same. The recent uptrend of the OneNote spear phishing campaign that SpiderLabs has observed since December 2022 has led us to additional investigations on this threat.
In this blog, we uncover the current attack techniques with the detection of network indicators and MITRE coverage.
For details about the initial decoy document, please refer to the TWSL blog Trojanized OneNote Document Leads to Formbook Malware.

Figure 1. Initial Decoy OneNote
Malware Campaigns
The current investigation starting January 31, 2023, shows the campaign is primarily delivering Qakbot and stealers like XWorm, Icedid, and AsyncRAT. We observed different infection chains with the PowerShell download cradle, VBS downloaders and batch file executions. Below are some of the techniques observed.
PowerShell Download Cradle:
- PowerShell download cradle -> Qbot DLL download -> Execute via Rundll32.exe -> Inject to process.

Figure 2. PowerShell download cradle - Method 1

Figure 3. PowerShell download cradle - Method 2

Figure 4. PowerShell download cradle - Method 3
VBS Downloader/Installer:
- exe -> VBS Downloader -> Download batch file with encrypted payload -> Drops PowerShell.exe as renamed -> PowerShell.exe decrypts and executes payload.

Figure 5. VBS Installer with PowerShell - Method 1
- exe -> JavaScript payload execution - > VBS script execution -> PowerShell download cradle downloads and executes payload.

Figure 6. VBS Installer with PowerShell - Method 2
Analysis of Qakbot aka Qbot
SpiderLabs has observed Qakbot more than any other malware variants. As of this date, we have observed five-bot campaigns from Qakbot with 264 C2s. Below is the analysis from the Qakbot file.
Qakbot Infection Flow
As seen from the above techniques, Qakbot was delivered using multiple downloading techniques with PowerShell or MSHTA predominantly used as the initial payload delivery.

Figure 7. Qakbot Infection Chain
- The initial decoy OneNote document is embedded with an ‘Open.cmd’ file.
- Upon execution of ‘Open.cmd’, it invokes the PowerShell download cradle.
- The hex encoded data is then decoded and passed to the parser to download the Qbot DLL.

Figure 8. PowerShell Download Cradle Parser
- Once downloaded, it will get executed with Rundll32.exe with the ‘Wind’ function.
- The Qbot packed DLL then injects into memory of process ‘grpconv.exe’ (‘msra.exe’ in some instances), and starts networking connections to Qbot C2’s.
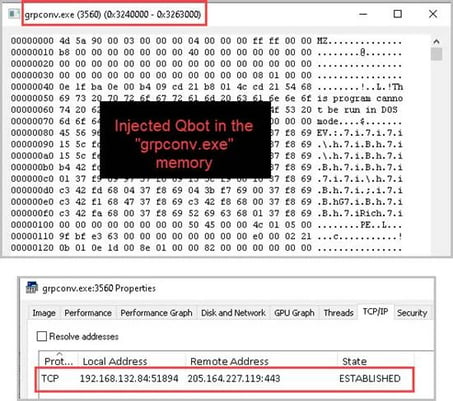
Figure 9. Qakbot Injected into ‘grpconv.exe’ Process.

Figure 10. Qakbot C2's Decrypted in Memory

Figure 11. Qakbot Post C2 Connections
- The encrypted data is stored in the registry. The key would be random and not in a readable format. The decrypted stored registry values show the Qbot campaign name and persistence created.
- The variant of Qbot malware will have its unique BotName tag for campaign identification. As of now we have five Qbot bot tags: BB12, BB14, BB15, tok01, and Obama239.

Figure 12. Decrypted Strings from Registry Shows the Qakbot Botnet Tag ‘BB15’
- The decrypted registry value shows the persistence to Qakbot DLL.

Figure 13. Decrypted Strings from Registry Shows the Qakbot Persistence
Decrypted Qakbot Strings from Memory
The decrypted Qakbot strings from memory show lots of their behaviors, some of which are:
- Querying for installed security products and running debuggers.

Figure 14. Decrypted Qakbot Strings

Figure 15. Checking for Installed Security Products and Debuggers Running
- Post infection data collected for profiling victim and sent to C2.

Figure 16. Post Infection Data Collected
- The memory dumps show more interesting traces like campaign name, persistence, victim bot-id, and C2 requests.

Figure 17. More info - Campaign Name, Persistence, Victim BotID
XWorm and Icedid
SpiderLabs has observed the usage of OneNote decoy documents by other malware variants like XWorm and Icedid. This is because they share a similar infection pattern along with VB Script payload installers.

Figure 18. XWorm Infection Flow

Figure 19. ICEdid Infection Flow
Detections
From the above infection flow, we can frame our detection rules custom to the working security appliances, some of which are:
- OneNote with child process ‘cmd.exe’ with command line contains ‘.cmd,.gif,.jpeg,.jpg,.pdf,.bat.'
- Multiple variants of PowerShell download cradles
- OneNote with child process ‘wscript.exe, mshta.exe.’
- A process events search for mshta.exe. In some cases, this will be run as a new instance.
- The command line contains ‘Rundll32’ and ‘.cmd,.gif,.jpeg,.jpg,.pdf,.bat.’
- Rundll32 events with DLLs run with ordinal functions ‘Wind’, ‘Updt’
- Rundll32 events with network connections are a good indicator.
- Rundll32 as parent process with any child (Suspected Injected Process) and having network connections.
The Rundll32 events will be noisy, but it is a good starting point for an investigation that, as a goal, is "Better safe than sorry."
MITRE Coverage
|
Tactic
|
Technique
|
|
Defense Evasion
|
File and Directory Permissions Modification - T1222
|
|
|
Obfuscated Files or Information - T1027
|
|
|
Obfuscated Files or Information: Indicator Removal from Tools - T1027.005
|
|
|
Rundll32 - T1218.011
|
|
|
Regsvr32 - T1218.010
|
|
|
Deobfuscate/Decode Files or Information - T1140
|
|
|
Mshta - T1218.005
|
|
|
Process Injection - T1055
|
|
|
Modify Registry - T1112
|
|
Discovery
|
File and Directory Discovery - T1083
|
|
|
System Information Discovery - T1082
|
|
|
System Location Discovery - T1614
|
|
|
Query Registry - T1012
|
|
Execution
|
Command and Scripting Interpreter - T1059
|
|
|
User Execution - T1204
|
|
|
Malicious File - T1204.002
|
|
|
Malicious Link - T1204.001
|
|
|
Windows Management Instrumentation - T1047
|
|
Initial Access
|
Spearphishing Attachment - T1566.001
|
|
Persistence
|
Registry Run Keys / Startup Folder - T1547.001
|
|
|
Scheduled Task - T1053.005
|
|
Command and Control
|
Application Layer Protocol - T1071
|
Conclusion
Once an adversary has successfully gained a foothold with their initial access being a phishing email, they must establish a backdoor and persistence. There are many ways to accomplish these feats, all while evading detection. Depending on what reconnaissance informs them and the intel they gather from their target’s environment, the tools they use to employ those techniques can vary. Therefore, it is ever important to remain vigilant and continually hunt for these behaviors.
Trustwave's recent revamp of its Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts and monitor our customers as this campaign continues. ACTH is now offered as an option in Trustwave's Managed Detection and Response Services. For more information, please read Trustwave Revamps Continual Threat Hunting Enabling Significantly More Hunts and Unique Threat Findings.
IOCs
IoCs for payload delivery URLs and Qakbot C2 IP Addresses are available here: https://github.com/SpiderLabs-Threat-Ops/SpiderLabs-Threat-Hunt/tree/main/Threat%20Indicators/OneNote_Campaign_February2023.



















