This is Part 8 in my ongoing project to cover 30 cybersecurity topics in 30 weekly blog posts. The full series can be found here.
If your organization has computers, and I’m sure it does, then it's likely it has an Endpoint Detection and Response (EDR) solution installed. Since the capabilities of EDR solutions have changed over the years, it’s recommended to re-evaluate the solution’s features periodically to ensure it is up to date. Let’s consider some of the facts, features, and choices to consider with EDR.
What is EDR?
EDR, or Endpoint Detection and Response, is the evolution of a collection of tools used to protect computers and servers. Back in the day, antivirus solutions met the standard of “good enough protection for computers” – i.e., an AV would compare files against a hash, and if it matched, the file would be quarantined or deleted. However, as hackers got smarter, so did the tools needed to detect their activities. As a result, EDR is now a multilayered architecture for detecting, investigating, and preventing malicious activity on operating systems.
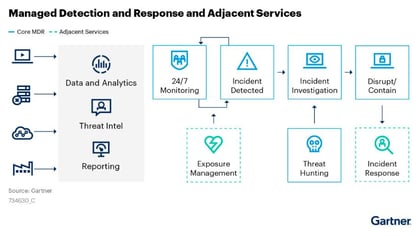
Image 1: MDR Enterprise Architecture.
What are the features an EDR may provide?
The EDR’s features will vary by vendor and cost. Since all organizations will need EDR, the sales market for these solutions is very aggressive and constantly evolving. Here are some of the most common features:
- MDR – Managed Detection and Response. Simply put, an MDR is an EDR, but provides API capabilities, that support management by an MSSP (Managed Security Services Provider).
- XDR – Integrates with other security services such as CASB, DLP, Identity Access Managers, and Endpoint Managers.
- Threat Hunting Tools – The ability to search the EDR activity using filters or a query language. Threat Hunting tools may provide automated searching using AI or by using a batch process to execute many searches at once.
- Automation – The EDR automatically investigates an alert and determines if it is a false positive, thus reducing the workload for a SOC operator. Other automated operations may include alerting or SOAR* operations.
- Mobile - Protection for mobile devices.
- Cloud Managed - All modern enterprise EDRs are cloud-based.
- Remote Control –Remotely connecting to an endpoint and execute commands for investigation or control.
- Network Detection – The EDR can monitor the local network and identify threats, traffic patterns and other network devices.
- AV – An AV component which matches files and processes against hashes.
- Shadow IT – Detection of devices installed without IT’s knowledge. These are less common, and possibly risky applications used by the endpoint.
- Web Monitoring – Detection of websites and applications connected over the network by the endpoint.
- White/blacklisting - Ability to allow or block processes, applications, IP addresses, etc.
- Vulnerability Scanning – Integration with a vulnerability analysis feature.
- ASR — Attack Surface Reduction – Advanced logic within an EDR that detects/blocks specific malicious activity within processes and memory.
How to choose the right EDR?
- Cost —This can be a complicated challenge, as every EDR vendor may have a different marketing strategy based on the customer’s size. So, it may be necessary to start with a less capable EDR solution and step up to a better version as budget and needs change.
- Existing licensing — Pro tip. If an organization is already using an enterprise license like Microsoft’s E5, a cost and feature comparison will likely favor that vendor’s EDR solution.
- Product Evaluation Reports — Unbiased organizations like Mitre EDR Evaluations provide evaluations on several EDR solutions. However, it’s important to look at both the scores and the underlying tests for these reports.
- XDR Capabilities — The XDR concept must be considered as hype vs reality. If you don’t have all the vendor’s solutions, the XDR value may be zero, or integration could be challenging and provide fewer features.
- NO EDR — Some organizations have bypassed the need for EDR by eliminating the endpoints. This is a very niche solution, but it is worth considering if the endpoint needs only kiosks, tablets, etc.
Additional thoughts about EDRs
EDRs:
1. EDRs aren’t a silver bullet. EDRs should be considered just one of many tools required for a full security defense architecture.
2. EDRs can be bypassed using techniques like ‘unhooking’. This means additional logging methods should be considered on critical servers or endpoints.
3. EDRs don't log every keyboard stroke. They depend on process monitoring, not human interaction.
4. Finally, EDRs can’t always detect zero-day attacks.
Summary
As EDR solutions evolve, it’s a good idea to review their cost vs. value. Understanding the full breadth of your security architecture is an important qualification for choosing and integrating EDR/MDR/XDR in an enterprise.
References
About This Blog Series
Follow the full series here: Building Defenses with Modern Security Solutions.
This series discusses a list of key cybersecurity defense topics. The full collection of posts and labs can be used as an educational tool for implementing cybersecurity defenses.
Labs
For quick walkthrough labs on the topics in this blog series, check out the story of “ZPM Incorporated” and their steps to implementing all the solutions discussed here.
Compliance
All topics mentioned in this series have been mapped to several compliance controls here.

