Agent Tesla's New Ride: The Rise of a Novel Loader
Malware loaders, critical for deploying malware, enable threat actors to deliver and execute malicious payloads, facilitating criminal activities like data theft and ransomware. Utilizing advanced evasion techniques, loaders bypass security measures and exploit various distribution channels for extensive impact, threat groups enhance their ability to download and execute various malware types as demonstrated by Smoke Loader and GuLoader, highlighting their role in extensive malware distribution.
Most recently, SpiderLabs identified a phishing email on March 8, 2024, with an attached archive that included a Windows executable disguised as a fraudulent bank payment. This action initiated an infection chain culminating in the deployment of Agent Tesla.
This blog provides an in-depth analysis of a newly identified loader, highlighting the attack's evasiveness and the advanced tactics, techniques, and procedures (TTPs) used in both the loader and its command and control (C2) framework. We will go through an in-depth discussion of the polymorphic nature of the loader, the use of specific user-agent strings, proxy usage, and command and control server protection that collectively enhances the loader's ability to deliver and execute the payload. While these techniques aren't new or unique individually, this new loader's effectiveness stems from its skillful combination and integration of these methods, which can potentially lead to increased infection rates and greater challenges for detection and mitigation.
Technical Analysis
Infection Chain
The following is a brief overview that illustrates the infection chain. The infection chain begins with a phishing email posing as a bank payment notification in which a disguised loader was attached as an archive file. This loader then used obfuscation to evade detection and leveraged polymorphic behavior with complex decryption methods. The loader also exhibited the capability to bypass antivirus defenses and retrieved its payload using specific URLs and user agents leveraging proxies for further obfuscate traffic. The payload itself, the Agent Tesla infostealer, is then executed entirely in memory, capturing and exfiltrating data via SMTP using compromised email accounts for discreet communication.
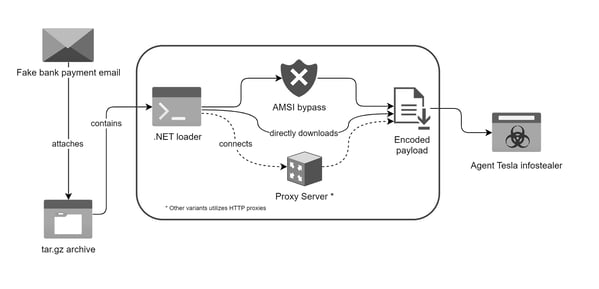
Figure 1. Infection chain: Email delivers loader, which then deploys Agent Tesla infostealer.
Email Delivery
The threat begins with a fake bank payment email designed to deceive recipients. Concealed within this email is an attachment named "Bank Handlowy w Warszawie - dowód wpłaty_pdf.tar.gz" masquerading as a legitimate payment receipt from a bank. This filename implies a harmless document, but it actually contains a malicious loader disguised within the tar.gz archive. This tactic is commonly employed in phishing attacks to trick recipients into unwittingly activating the malware and initiating nefarious activities.

Figure 2. MailMarshal unpacking tar.gz attachment from fake product email.
Loader
The loader executable, compiled with .NET, uses obfuscation and packing to hide its functionality and evade detection.
Upon execution, the loader initializes its configuration by storing encrypted strings and decryption keys in separate lists within its code. The decryption begins by identifying an encrypted string's index and matching it to a specific key in another list. This index-based matching is a crucial step in decrypting the configuration data the malware needs to operate.
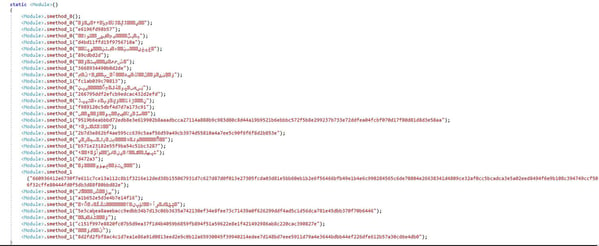
Figure 3. Variant 1: Encrypted configuration and strings of the loader

Figure 4. Variant 2
The loader's polymorphic behavior is particularly intriguing, evident through two distinct variants we observed, each utilizing a different decryption routine. This polymorphism introduces an additional layer of complexity, posing significant challenges for traditional antivirus systems.
Taking a closer look at the decryption routines employed by each variant reveals the intricacies of their operations:
Variant 1 - ab9cd59d789e6c7841b9d28689743e700d492b5fae1606f184889cc7e6acadcc
The first variant decrypts the configuration by converting the hexadecimal key into a byte array. It then generates an SHA-256 hash of the encrypted string, ensuring the hash's length matches that of the byte array from the key. Following this, it then decrypts by subtracting corresponding bytes in the key-derived byte array from those in the SHA-256 hash.

Figure 5. Variant 1: Decrypts using hex string conversion, SHA-256 hashing, and subtraction.
Variant 2 - a02388b5c352f13334f30244e9eedac3384bc2bf475d8bc667b0ce497769cc6a
The second variant’s decryption process begins by converting the key from base64 and the encrypted string into bytes. It then performs a bitwise XOR operation on the corresponding bytes of the key and the encrypted string. The resulting byte array is re-encoded into UTF-8 to produce the decrypted string.
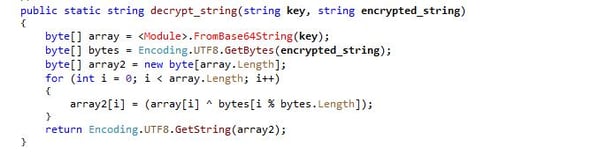
Figure 6. Variant 2 Decryption: base64 key, string conversion and XOR operation.
The loader's configuration hides key functions and libraries, notably VirtualProtect from kernel32.dll, to modify memory permissions for code injection. It uses encoded references like amsiScanBuffer and amsi.dll to obscure its attempt to bypass Microsoft's Anti-Malware Scan Interface (AMSI) detection.
Furthermore, terms such as Invoke, EntryPoint, Load, Assembly, and GetType referpoint to reflective loading, which allows for dynamic code execution at runtime.
Additionally, the configuration includes the download URL and User-Agent string, pivotal for retrieving payloads.
Antivirus Evasion via AMSI Bypass
Before initiating the payload retrieval and reflective loading processes, the loader prepares the target system to ensure seamless payload execution. This preparation includes bypassing the Antimalware Scan Interface (AMSI) by patching the AmsiScanBuffer function to evade malware scanning of in-memory content.
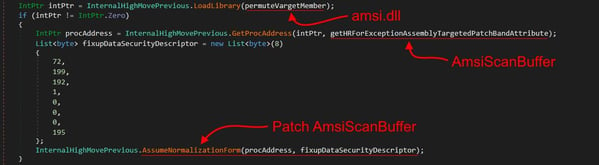
Figure 7. AMSIScanBuffer bypass via memory patching.
Payload Retrieval and Execution
Following the AMSI bypass, the loader prepares the memory space for the incoming payload. It specifically targets the payload hosted at hxxps[://]artemis-rat[.]com, requiring a specific user-agent string, Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, killer Gecko) Chrome/58.0.3029.110 Safari/537.3, to ensure the delivery of the payload.
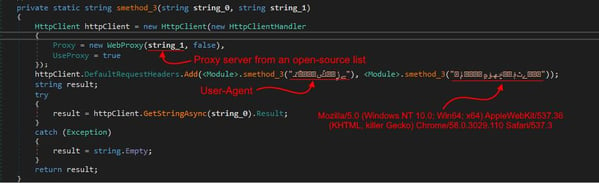
Figure 8. Variant 1 utilizes a specific-user agent to fetch payload though a proxy.
One variant employs an HTTP proxy server sourced from an open-source list on GitHub, specifically from https://github.com/TheSpeedX/PROXY-List/blob/master/http.txt, to facilitate the download of the payload. This approach generates numerous network packets and significant noise, potentially complicating network traffic analysis and detection efforts.
After retrieval, the payload is not executed immediately. Instead, the loader identifies and extracts the payload from HTML content using “:::” as a delimiter to separate the malicious code. This operation segment underscores the loader's stealthy approach in handling the payload, ensuring that the malicious code remains undetected within benign-looking traffic. Following extraction, the payload is loaded into memory.

Figure 9. The encoded payload embedded within the body of the HTML response.
The loader decrypts the payload using XOR encryption, with the decryption key embedded within the loader itself. It begins by converting the hexadecimal string into a byte sequence, then iterates over each byte, applying the XOR operation with the corresponding byte in the key. The two variants we observed follow a similar decryption routine to process the payload, differing only in the decryption keys used.
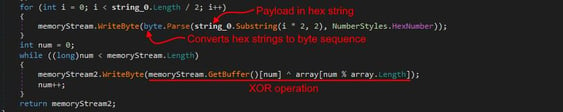
Figure 10. Payload decryption routine
Once the payload is decoded and stored in memory, the loader, utilizing .NET's reflection and assembly loading capabilities, locates and invokes the main entry point of the payload, triggering the operation of the Agent Tesla infostealer. The loading and execution process takes place exclusively within the system's memory space, minimizing detection and leaving no trace on disk, thus enhancing the stealth and evasiveness of the malicious activity.
Agent Tesla Infostealer
Agent Tesla is executed entirely from memory, conducting malicious activities like keystroke logging, credential theft, and data exfiltration. This variant uses KoiVM protector, a virtualization-based packer that transforms .NET CIL code into virtual instructions, which is interpreted at runtime by a virtual machine, complicating both static and dynamic analysis.
After collecting valuable information like usernames and passwords from web browsers, Agent Tesla exfiltrates this data using the Simple Mail Transfer Protocol (SMTP), a method commonly used for sending emails.
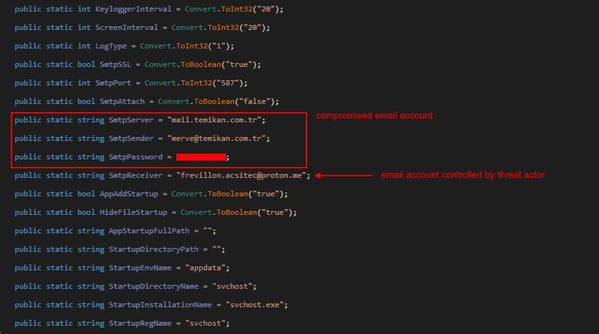
Figure 11. Embedded configuration of Agent Tesla infostealer
Threat actors often hijack compromised email accounts to carry out the exfiltration process. This method has several strategic benefits. First, it exploits the trust people have in regular email communication, making it less likely to raise suspicion. Second, it provides anonymity and makes it harder to trace the attack back to the threat actors. Finally, using existing email systems means they don't have to set up new communication channels, saving time and resources.
Summary
The new loader observed in conjunction with Agent Tesla utilizes deceptive email attachments, such as a disguised bank payment receipt, to infiltrate systems. Compiled with .NET, it employs obfuscation and packing techniques to conceal its functionality and evade detection. The loader exhibits polymorphic behavior with distinct decryption routines. It employs methods like patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, ensuring stealthy execution and minimizing traces on disk. This loader marks a notable evolution in the deployment tactics of Agent Tesla.
Furthermore, given its versatility, it is likely that this loader will be utilized to deploy other types of malware beyond Agent Tesla in the future.
Indicators of Compromise
Loader (Variant 1)
MD5 b69f65b999db695b27910689b7ed5cf0
SHA256 ab9cd59d789e6c7841b9d28689743e700d492b5fae1606f184889cc7e6acadcc
Loader (Variant 2)
MD538d6ebb40197248bc9149adeec8bd0e7
SHA256a02388b5c352f13334f30244e9eedac3384bc2bf475d8bc667b0ce497769cc6a
Packed Agent Tesla
MD52bd452c46a861e59ac151a749047863f, 63f802e47b78ec3d52fe6b403bad823f
SHA256 e3cb3a5608f9a8baf9c1da86324474739d6c33f8369cc3bb2fd8c79e919089c4, f74e1a37a218dc6fcfabeb1435537f709d742505505a11e4757fc7417e5eb962
Unpacked Agent Tesla
MD5 3637aa1332b312fe77cc40b3f7adb8dc, 37b38ae2d99dd5beb08377d6cbd1bccd
SHA256 3a1fe17d53a198f64051a449c388f54002e57995b529635758248dc4da7f5080, a3645f81079b19ff60386cb244696ea56f5418ae556fba4fd0afe77cfcb29211
SMTP Exfiltration
Sender email: merve@temikan[.]com[.]tr
Receiver email: frevillon[.]acsitec@proton[.]me
Download URLs
hxxps[://]artemis-rat[.]com/get/65f0e7dd5b705f429be16c65
hxxps[://]artemis-rat[.]com/get/65eb0afe3a680a9851f23712
User-Agent
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, killer Gecko) Chrome/58.0.3029.110 Safari/537.3
List of Proxy Servers
hxxps[://]github[.]com/TheSpeedX/PROXY-List/blob/master/hxxp[.]txt
Table 1. First loader variant's decrypted strings
|
Invoke EntryPoint Load Assembly GetType VirtualProtect kernel32[.]dll {0}A{1}m{2}s{3}i{4}S{5}c{6}a{7}n{8}B{9}u{10}f{11}f{12}e{13}r{14} {0}a{1}m{2}s{3}i{4}.{5}d{6}l{7}l{8} AssalamAlaikum ::: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, killer Gecko) Chrome/58.0.3029.110 Safari/537.3 User-Agent hxxps[://]artemis-rat[.]com/get/65eb0afe3a680a9851f23712 \d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}:\d{1,5} hxxps[://]github[.]com/TheSpeedX/PROXY-List/blob/master/hxxp[.]txt |
Table 2. Second loader variant's decrypted strings
|
::: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, killer Gecko) Chrome/58.0.3029.110 Safari/537.3 User-Agent Invoke EntryPoint Load Assembly GetType hxxps[://]artemis-rat[.]com/get/65f0e7dd5b705f429be16c65 {0}A{1}m{2}s{3}i{4}S{5}c{6}a{7}n{8}B{9}u{10}f{11}f{12}e{13}r{14} {0}a{1}m{2}s{3}i{4}.{5}d{6}l{7}l{8} Load Assembly GetType |
About the Author
Bernard Bautista is Security Researcher, SpiderLabs at Trustwave, where he specializes in email and malware analysis. He focuses on improving the security posture of customers by analyzing email-borne threats and developing detection mechanisms to protect against emerging cyber threats. Follow Bernard on LinkedIn.
ABOUT TRUSTWAVE
Trustwave is a globally recognized cybersecurity leader that reduces cyber risk and fortifies organizations against disruptive and damaging cyber threats. Our comprehensive offensive and defensive cybersecurity portfolio detects what others cannot, responds with greater speed and effectiveness, optimizes client investment, and improves security resilience. Learn more about us.
